2-Party SSO Flow¶
This flow, based on the authorization code flow defined in RFC6749 Section 4.1 is used to persist a guest’s SSO between one integration and another. For example, a guest logs into an integrated mobile app and navigates to a different integrated online ordering website. SSO is persisted without needing the guest to sign in again.
To authenticate a guest using an authorization code¶
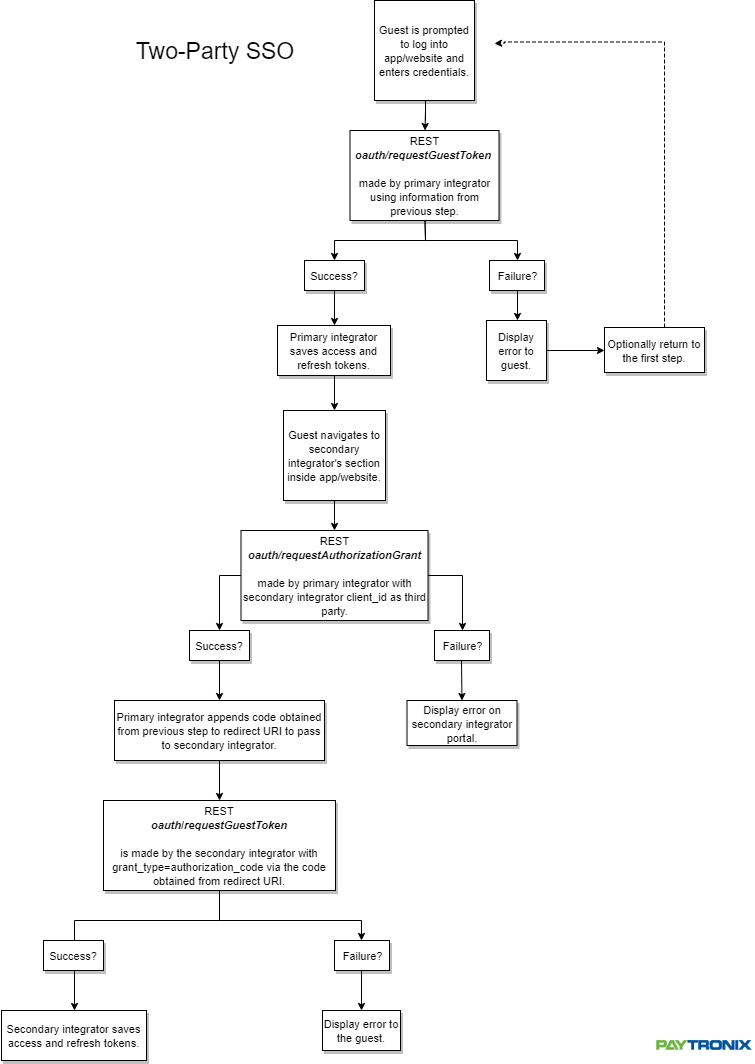
User logs into the 1st party’s integration (such as an integrated mobile app)
- Once logged in, guest taps on a link to navigate to the 2nd party’s integration (such as an online ordering webview). This should trigger the 1st party integration to make a
POST oauth/requestAuthorizationGrant.jsonAPI call, and append the resultingauthorizationGrantas a query param to the URL in the link. This auth grant is one-time-use and expires 5 minutes after being generated. eg. https://myawesomesite/login?code=APA91bFdV3CWmJpMors50gWwQqtmmwxYKpyy1&expires_in=300
- Once logged in, guest taps on a link to navigate to the 2nd party’s integration (such as an online ordering webview). This should trigger the 1st party integration to make a
- The 2nd party integration should then make a requestGuestToken call by auth grant to the Paytronix to obtain an access and refresh token pair.
- If the result is a success, Paytronix will return the guest’s username, an access token and a refresh token. The access token may then be used to authenticate functionality such as account balance and user information.
- If the result is a failure, an error should be provided to the guest. Paytronix will include additional information regarding why the message failed.
See Grant By Authorization Grant for more information